Discover Ingenious Safety And Security with BQT Solutions for All Your Requirements
Wiki Article
Maximizing Service Protection: The Ultimate Guide to Electronic Protection Solutions
In the fast-paced and ever-evolving landscape of organization safety and security, the reliance on digital protection services has ended up being paramount for protecting beneficial possessions, confidential information, and preserving functional connection. In this guide to electronic protection options, we will certainly explore the most current fads, sophisticated innovations, and ideal methods to strengthen your business against potential risks and susceptabilities.Value of Electronic Protection Solutions
When taking into consideration the protection of assets and delicate details, the value of digital safety and security options can not be overstated. In today's interconnected world, where cyber threats are regularly advancing and coming to be more innovative, organizations need to prioritize executing robust electronic safety and security measures to protect their information and operations. Electronic safety solutions include a vast array of innovations and practices made to resist unauthorized access, data breaches, malware, and other cyber hazards.Among the key advantages of digital safety options is their ability to provide real-time monitoring and hazard detection. BQT Sideload locks. Via tools like breach discovery systems, firewall softwares, and safety details and event monitoring (SIEM) systems, companies can proactively recognize and react to security occurrences before they intensify right into major breaches. Additionally, electronic safety and security remedies assist guarantee compliance with sector laws and criteria, safeguarding companies from potential legal and financial repercussions
Kinds Of Electronic Security Equipments
Offered the vital value of electronic safety and security remedies in safeguarding companies versus cyber threats, it is essential to discover the different kinds of digital safety and security systems readily available to enhance defense and strength. One of the most common types of digital safety and security systems is the firewall, which acts as an obstacle in between a firm's internal network and outside networks, filtering system out possibly harmful information. By utilizing a mix of these electronic protection systems, services can develop a durable protection versus different safety hazards.Executing Access Control Actions
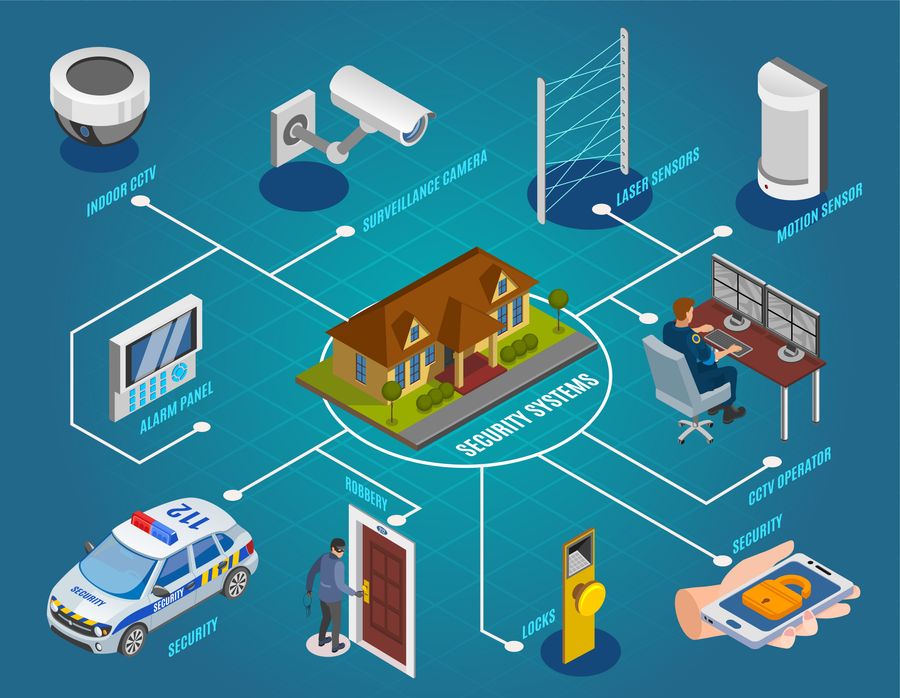
Furthermore, accessibility control actions can be incorporated with security systems to check and tape-record people' movements within protected areas. This assimilation improves safety by supplying an extensive summary of who is accessing specific places at any kind of provided time. Access control systems can be configured to limit accessibility based on time, location, or individual credentials, allowing organizations to customize protection methods according to their details requirements.
Cybersecurity Ideal Practices
To improve total safety pose, applying robust cybersecurity best practices is imperative in securing electronic possessions and information integrity. One fundamental practice is ensuring routine software application updates throughout all tools and systems to patch susceptabilities without delay. Employing strong, unique passwords and implementing multi-factor verification includes layers of protection versus unapproved access. Performing regular safety and security audits and assessments helps recognize weaknesses and locations for enhancement. Staff member training on cybersecurity recognition is vital in stopping social design attacks and guaranteeing a security-conscious labor force.Developing a detailed event feedback plan makes it possible for swift and efficient reactions to safety and security violations, decreasing possible damages. Applying access controls based on the principle of the very least privilege restricts the direct exposure of vital systems and info to just those that require it for their roles. By including these best practices into cybersecurity techniques, services can strengthen their defenses against progressing cyber risks.
Surveillance and Monitoring Solutions

Video security options offer remote tracking abilities, allowing licensed employees to watch on the facilities even when off-site. Additionally, progressed functions like activity discovery, face recognition, and certificate plate recognition boost the total security pose of the company. Integrating monitoring systems with alarm and gain access to control better strengthens the safety and security facilities, enabling BQT Solutions an aggressive feedback to potential safety and security breaches.
Final Thought
In conclusion, digital safety solutions are important for making best use of organization protection. It is vital to spend in the appropriate digital protection systems to make certain the security and safety of the company.Report this wiki page